Published on: May 14, 2019 by Albert Reilly

Scenario:
Sending unwanted bulk messages indiscriminately by using electronic messaging systems like email, instant messaging or mobile and text messaging is called spamming. In other words, sending information to someone who has not requested that from you.
The first documented spam was an email advertising the availability of a new model of Digital Equipment Corporation computers. It was sent by Gary Thuerk to 393 recipients on ARPANET in 1978. He had an assistant, Carl Gartley, write a single mass email Rather than sending a separate message to each person, which was the standard practice at the time.
It was initially used frequently with commercial content, in large quantities and later evolved to spread computer viruses, Trojan horses or other malicious software. The objective varies from identity theft to advance fee frauds. Some spam takes advantage of the victims’ inexperience with computer technology while some attempts to capitalize on human greed.
According to records, spam in email started to become a problem in the mid-1990s and by 2007 it composed some 80 to 85 percent of all email and decreased to 66 percent in 2014.
Anti-spam refers to services and solutions that concentrate on blocking and mitigating the consequences of illicit emails or spam on email users. to realize this objective, differing kinds of anti-spam systems are integrated with the email systems of the many email and Internet Service Providers (ISP).
Modern anti-spam technology covers a broad spectrum of filters, scanners and different kinds of applications. Some anti-spam services work from a statistical method, whereas others use heuristics or predictive algorithms. To sort email in sophisticated ways, anti-spam service providers could monitor email signatures, IP addresses or different information, that reduces spam.
The emergence of anti-spam software system adds to the continuing conflict between email recipients and uninvited email senders. ISPs and email providers are operating to secure legislative victories that would block certain sorts of email promoting. However, senders could notice ways in which a message’s origins are protected or imitate another sender’s signature or different email features. Likewise, senders could find ways to combat anti-spam tool algorithms and break through filters to reach email users. There are techniques like using RBLs, Tarpitting, Spam Trap or using third-party software as a solution.
A network security and optimization process through which network administrators (NA) intentionally slow down the propagation of mass emails by restricting and demotivating spammers from sending bulk messages is called tarpitting. It works when a server identifies a client’s abnormal email operations, which can be sending thousands of emails in a very limited period and then slows down the process, eventually preventing spammers from succeeding.
The trap is essentially a honeypot that distinguishes spam by creating an email address configured, unpublished or not subscribed to receive email. This valid email is kept private to the spam analyzer or legitimate persons. All incoming emails sent to this email are considered unsolicited or spam, which therefore helps to identify spam email and those who send it.
The messages or emails are classified as spam by comparing the content with a known database of words that are considered to be included in common spams rather than enforcing across-the-board policies for all messages from a particular email or IP address. However, these types of filters may generate false positives if configured to block messages containing more common words.
A special kind of software package, software extension or maybe a simple technique that is designed to block uninvited bulk emails, or spam is termed spam blocker, also referred to as a spam filter. Some spam blockers are real programs, although small, whereas some are merely custom configurations in an email client’s filter function. Spam blockers and filters have lists that contain the address that is either allowed to pass through or blocked. Addresses that are allowed to pass are placed on the “whitelist,” whereas those that are supposed to be blocked are placed within the “blacklist.”
A spam mail can be easily identified by checking the subject, Recipient address, or the contents. It can be advertisements, adult contexts, or any other unnecessary content. Note that some websites may send advertisements, adult contexts etc.. to their recipients. So always check other possibilities before confirming. Most spam is sent using a script. thus we narrow our search to spamming scripts only. With CMS like Magento, Joomla, and WordPress, it’s become easier for malicious users to upload files to users accounts through outdated plugins or base versions installed on the account.
Check the mail queue. Larger mail queue indicates the possibility of spam.
exim -bpcTo get details of emails in the queue, remove the option c. The output will be similar to as below.
33m 1.3K 1geeLm-00076Z-5K <userx1@domainx1.com> user@domainx2.com
33m > This denotes how much time the message has been stuck in the queue. 1.3K > This is the size of the message. 1geeLm-00076Z-5K > This is is the message ID. This is something needed for debugging the spamming issue. userx1@domainx1.com > This is the account from which spam mail is sent. user@domainx2.com > This is the email account to which spam emails are sent.
Now we will review the mail. First, evaluate the header and check the subject, from address and also check for the string “X-PHP-Script”. This string indicates that the mail has been sent using a PHP script.
Note: X-PHP Script shown will not always be spam, there may be cases where newsletters are sent using a script or it may be the cron daemon. You need to manually check it and verify the same.
exim -Mvh <message_id>If the header is found relevant or genuine or there is no X-PHP-Script, you can move on to analyze the body.
exim -Mvb <message_id>Check if the body of the content is related to the site to verify it is spam or not if you have any doubts. You can also check with the site owner to verify it is genuine or not.
You can delete emails of the spamming user from the queue.
exim -bp | grep <username> | awk'{print $3}'| xargs exim -Mrm
To check if any spam emails were sent from the server, we will need to check the Exim mail log (exim_mainlog) as they are not found in the queue. A good approach is to list the last 100 lines of the exim_mainlog and then check if any user is suspiciously sending a large number of emails.
tail -f -n100 /var/log/exim_mainlogIf found, analyze the subject or topic (T=””) from the output. You can have a look at https://forums.cpanel.net/resources/reading-and-understanding-the-exim-main_log.383/ to get an idea of how to read Exim logs.
Check the CWD (Current Working Directory) of that mail from the output. A path like /home/username/ indicates that the mail has been sent by some script in that directory. You can also use the below command to find the CWD of a particular user.
grep <username> /var/log/exim_mainlog | grep "cwd=" | tail 2019-01-02 21:26:17 cwd=/home/userx1/public_html 4 args: /usr/sbin/sendmail -t -i user@domainx2.comSo we will move on to find that script. The may be named mailer.php or something similar. You will need to open and check for clarity. After verification, you can change the permission to 000 or rename to .back and inform the client. Initiating a malware scan can help.
ls -lahtr /home/userx1/public_htmlYou can use the below command and list the IPs that are accessing the script currently and can block them if needed.
grep "mailer.php" /home/userx1/access-logs/domain.com | awk '{print $1}' | sort -n | uniq -c | sort -nThis will search the Exim log from beginning and pull back a list of sites and the number of emails they have sent wih the CWD.
grepcwd/var/log/exim_mainlog | grep -v /var/spool | awk -F"cwd=" '{print $2}' | awk '{print $1}' | sort |uniq-c | sort -n
The information will look like this
4 /home/userx18/public_html
4 /home/userx21
4 /home/userx3/public_html
6 /home/userx42/public_html
9 /home/userx5
9 /home/userx6
10 /home/userx7/public_html
11 /home/userx84/public_html
27 /home/userx22/public_html
29 /home/userx10
32 /home/userx15
34 /home/userx12
36 /home/userx16
36 /home/userx14
72 /home/userx19
1089 /home/userx1/public_html
Go on and find the script and back it.
ls -lahtr /home/userx1/public_htmlPreventing is always better than cure. For preventing spam in a new server, we can employ third-party software like SpamExperts, ASSP Deluxe or SpamStopsHere. In this part, some prevention methods like using SpamExperts for spam protection, setting RBLs in WHM, setting DNS records etc are described. Although cPanel has SpamAssassin, the built-in feature usually offer less performance and thus third party software is used for relay servers or for individual servers.
Employing third-party software and maintaining separate databases can become costly and require some additional work. So an alternative method is to set RBLs in WHM. Go to WHM > Exim Configuration Manager in Server Configuration.
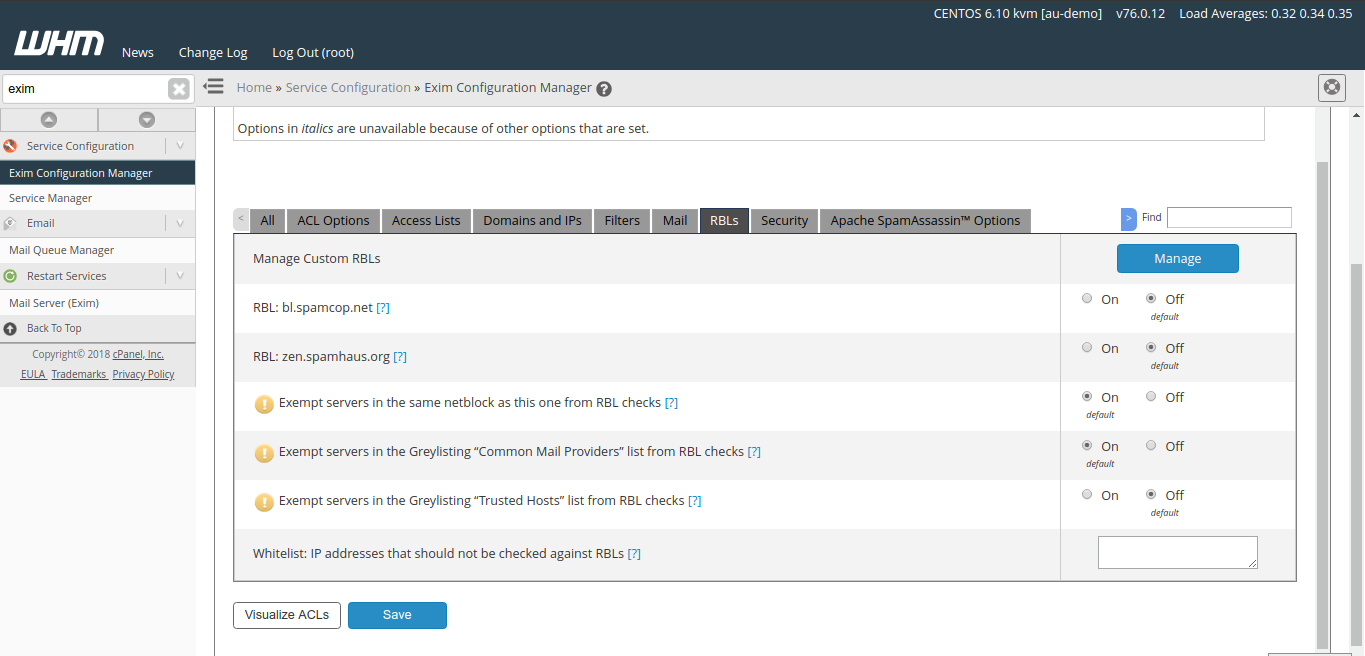
Custom RBL can be set by clicking Manage button.
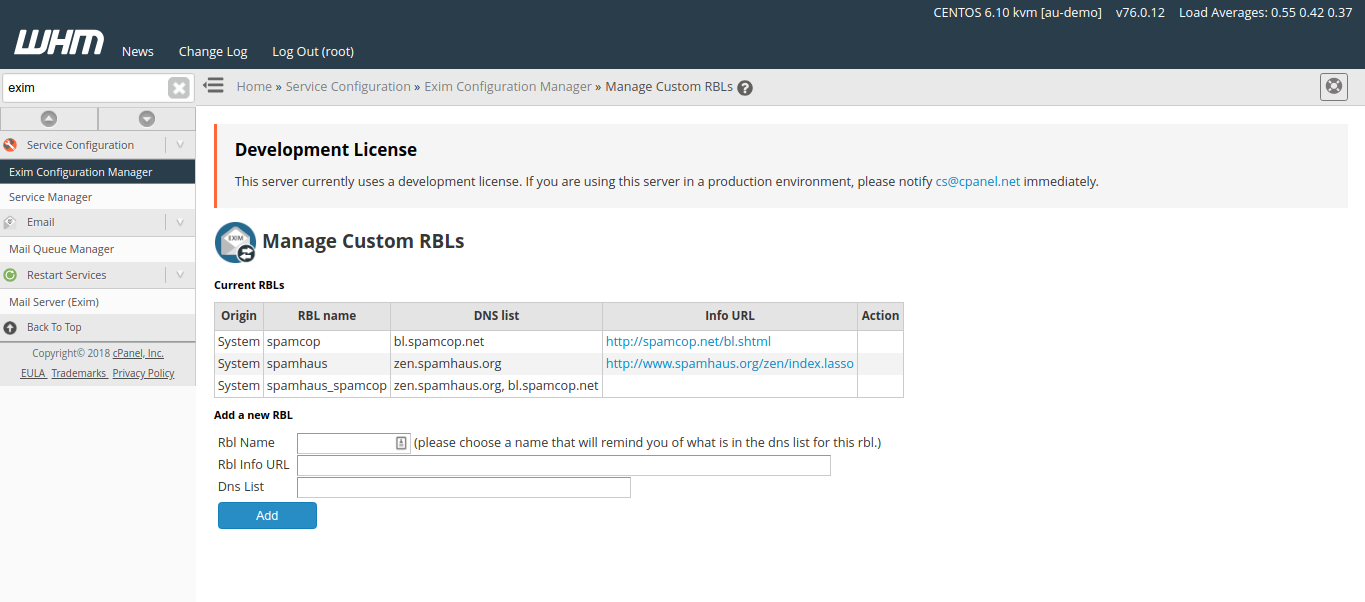
Below is a list of some RBLs that can be added.
| DNS list | Info URL |
|---|---|
| zen.spamhaus.org | http://www.spamhaus.org/zen/ |
| rhsbl.ahbl.org | http://www.ahbl.org/documents/rhsbl |
| truncate.gbudb.net | http://www.gbudb.com/truncate/ |
| b.barracudacentral.org | http://www.barracudacentral.org/account/register |
| bl.blocklist.de | http://www.blocklist.de/en/api.html#dns |
| dnsbl.dronebl.org | http://dronebl.org/docs/howtouse |
| dnsbl-1.uceprotect.net | http://www.uceprotect.net/en/index.php?m=6&s=10 |
| all.s5h.net | http://www.usenix.org.uk/content/rbl.html |
| ubl.unsubscore.com | http://blacklist.lashback.com/ |
| new.spam.dnsbl.sorbs.net | http://www.sorbs.net/lookup.shtml |
| nomail.rhsbl.sorbs.net | http://www.sorbs.net/lookup.shtml |
| zombie.dnsbl.sorbs.net | http://www.sorbs.net/lookup.shtml |
| srnblack.surgate.net | https://tools.korumail.com/ |
You can follow the documentation to set custom mail filters in cPanel. This will only work if SpamAssassin is enabled.
Custom Email Filtering across cPanel server
For reference and to get to know the fields, you can follow the cPanel documentation at
https://documentation.cpanel.net/display/CKB/How+to+Configure+Mail+Filters.
Spam can be filtered using the challenge-response verification process with the help of a tool called BoxTrapper from cPanel > BoxTrapper under the Email section. When it is enabled, the sender receives a verification email and he must complete the verification process before the email can pass through to the inbox. To setup, you can refer the below cPanel documentation.
https://documentation.cpanel.net/display/68Docs/BoxTrapper
You can follow the cPanel documentation
https://documentation.cpanel.net/display/CKB/How+to+Prevent+Spam+with+Mail+Limiting+Features
and make use of the Mail limiting feature in WHM >> Home >> Server Configuration >> Tweak Settings for limiting the number of emails sent by users.
Several anti-spam methods use the domain name system (DNS) to identify and foil spammers. If the emails are going to the spam folder, by viewing the mail header will get you an idea about the reason why that mail is going to spam. Three records are mainly to be considered, with three possible status – Fail, Success, Neutral.
Instead of following the below steps to add records, you can do this in one click from cPanel’s Authentication interface (cPanel > Authentication), allowing you to enable or disable Domain Keys Identified Mail (DKIM) and Sender Policy Framework (SPF)
How to Keep your Email out of Spam?
You can go to
https://documentation.cpanel.net/display/68Docs/Authentication
for more details.
SPF:
It specifies a list of authorized hostnames/IP addresses that mail can originate from for a given domain name. A neutral record is less probable to be the reason for emails going to spam.
Eg: v=spf1 ip4:204.200.197.197 -all
DKIM:
It attaches a new domain name identifier to a message and uses cryptographic techniques to validate authorization for its presence. You can regenerate a new DKIM record by following the below steps:
ssh-keygen
Record type: TXTHostname: default._domainkeyText value: v=DKIM1; p=yourPublicKey(new_generated)
Eg: v=DKIM1\; k=rsa\; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQC3QEKyU1fSma0axspqYK5iAj+54lsAg4qRRertyK68hawSd8zpsDz77ntGCR0X2mHVvkf0WEOIqahdgr/A5IGxieiWer+wBX8lW2tE4NHTE0PLhHqL0udioh62pKoPR3Wr6n/rbiihGYCIz1d8f36/U5GigNUGls/QUbCPRyzho30wIDAQAB
Yahoo uses Spamhaus to track email spammers and spam-related activity. If the IP is listed, then you need to request removal from Spamhaus before you contact Yahoo.
https://www.spamhaus.org/lookup/
Next thing is to complete the Yahoo Bulk Sender Form. It is best to provide as much information as possible in a short and precise way in the form.
Hotmail/Outlook uses the Brightmail anti-spam content filter. Check Brightmail IP reputation and request the block removal if you are listed.
http://ipremoval.sms.symantec.com/lookup/
Complete the Sender information form and provide all of the requested information. If you provide reliable information and are truly not spamming their users, you will typically see your IP removed from the blacklist in 2-3 business days.
https://support.microsoft.com/en-us/supportrequestform/8ad563e3-288e-2a61-8122-3ba03d6b8d75
Additionally, you can check for IP blocks in different global RBLs using the below link.
https://mxtoolbox.com/blacklists.aspx
SpamExperts is one of the commonly used and intelligent spam filtering services. It uses many factors to determine if an incoming or outgoing message is safe. It includes Greylisting, Real-time blacklists (RBLs), Content analysis and SPF and DKIM testing. SpamExperts add-ons are available for a number of different hosting control panels such as cPanel, Odin Service Automation, Plesk, MachPanel, DirectAdmin and more.
The below documentation from SpamExperts explains how to set up the cPanel addon.
Setting Inbound rules and filtering incoming emails can be done following the SpamExperts documentation.
Setting Outbound rules and filtering outgoing emails can be done following the SpamExperts documentation.
https://documentation.solarwindsmsp.com/spamexperts/documentation/qsg/Content/qsg/qsg-out-filter.htm
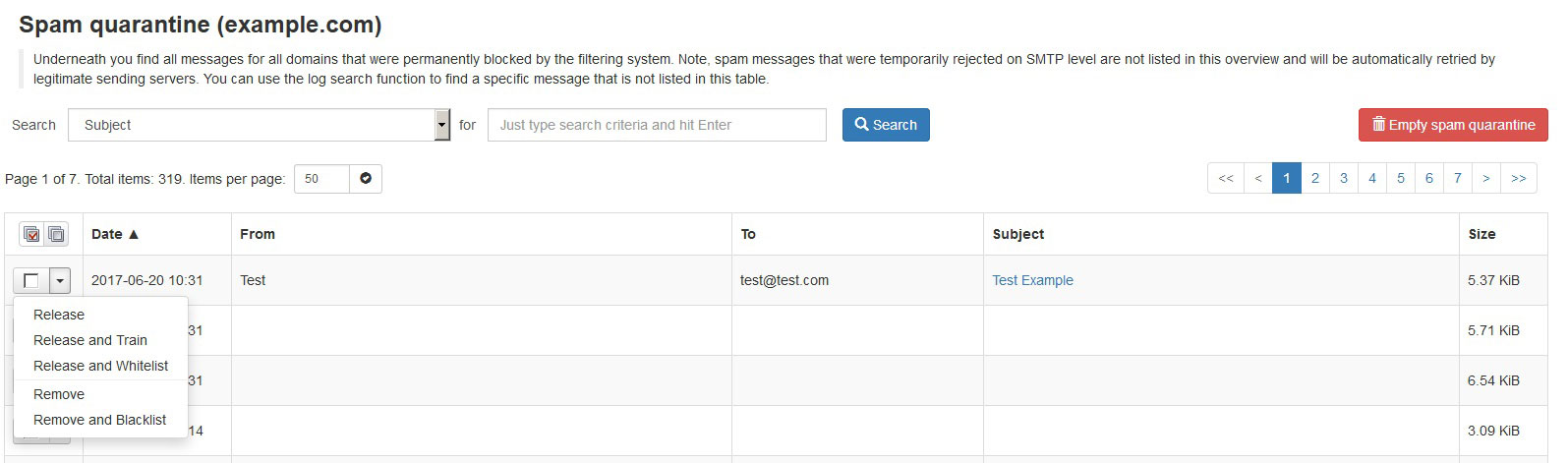
You can identify the delivery status of the email by checking the delivery log (both incoming and outgoing). Once logged in to SpamExperts, look for log search icon and you will get a comprehensive set of search parameters.
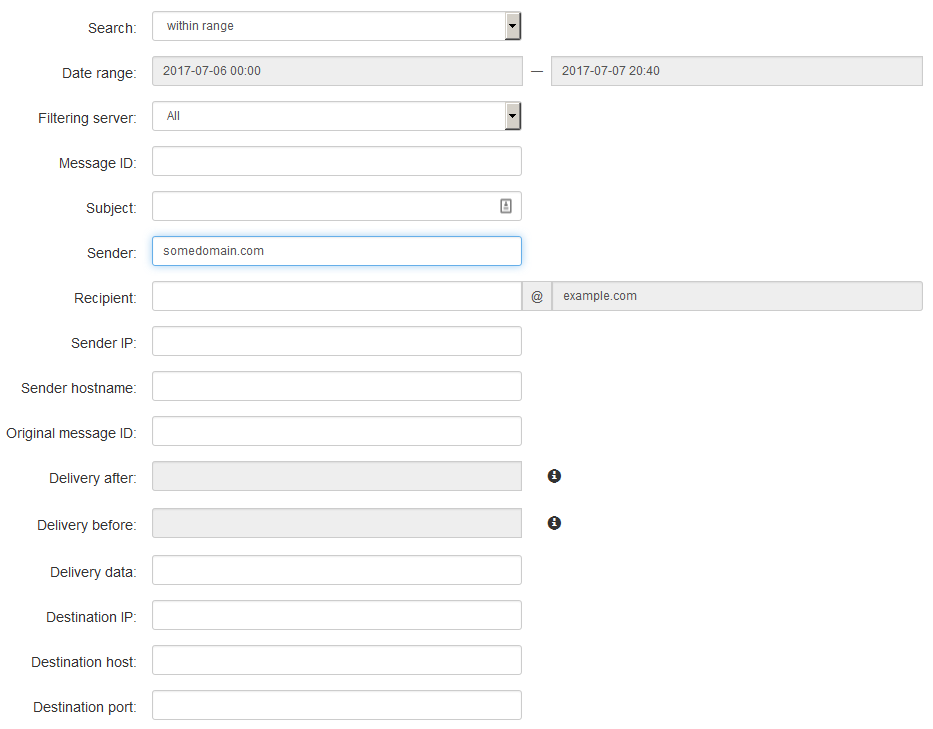
You do not have to use all of them but the broader your search, the more records will be returned. You have the option to set the date range, filtering server, Message-ID, Subject, and all. Additionally, you can set the message classification (spam, virus, differed, etc), the current status of the message, Any or All condition match and option to return partial matches.
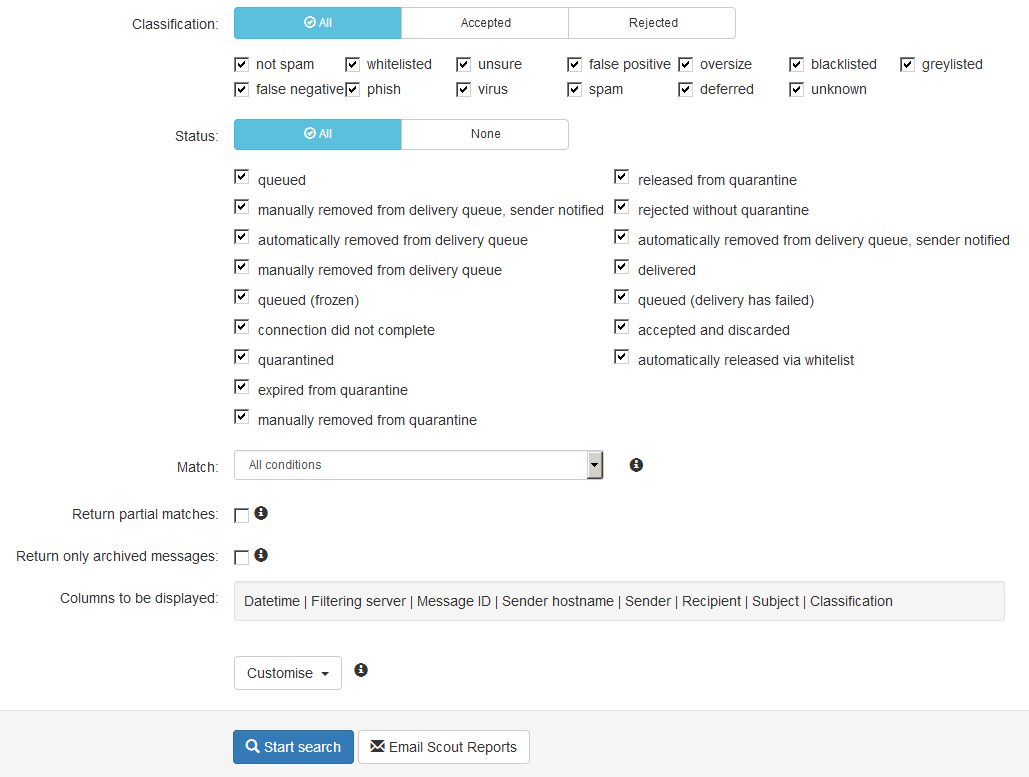
After getting the results, you will have the options to Release the mail if blocked, Release and train, remove it or remove and blacklisting.
Similar to SpamExperts are SpamStopsHere and ASSP Deluxe. Both have different features and options and are recommended by cPanel. For configuration, you can refer the below links:
SpamStopsHere
https://www.spamstopshere.com/spam-filter/easy-setup.html
ASSP Deluxe
http://www.grscripts.com/howto130.html
In certain situations, we need a temporary email id to subscribe to something or for testing purpose. Then we employ an approach where a unique email address is generated and used. The benefit is that if anyone compromises the address or utilities it in connection with email abuse, the address owner can easily cancel or dispose of it without affecting any of their other contacts.
You can go to these links to get a temporary email id.
https://www.tempmailaddress.com/
https://temp-mail.org/en/
https://www.throwawaymail.com/
From this article, we will get a general idea of spamming and why it is used. Some common anti-spamming techniques like content filtering and Spam Blockers are described. Spam identification is described. There are some spam mitigation techniques commonly used in cPanel and is described along with their implementation.
Category : cPanel

Add new commentSIGN IN