Published on: May 24, 2023 by TECH

Scenario:
AWS CloudFormation provides you with a simple way to create and manage a collection of AWS resources by provisioning and updating them in an orderly and predictable way. In simple terms, it allows you to create and model your infrastructure and applications without having to perform actions manually.
AWS CloudFormation enables you to manage your complete infrastructure or AWS resources in a text file, or template. A collection of AWS resources is called a stack. AWS resources can be created or updated by using a stack.
The following guide will go through the steps involved in setting up a cloudformation template to create multiple S3 buckets.
Create a new template or use an existing CloudFormation template using the JSON or YAML format.
Here, I’m using a new template in YAML format, copy and paste the following code to make the YAML template.
AWSTemplateFormatVersion: 2010-09-09
Description: AWS CloudFormation template - to create S3 buckets.
Parameters:
BucketNameParameter1:
Type: String
Description: Bucket Name
BucketNameParameter2:
Type: String
Description: Bucket Name
BucketNameParameter3:
Type: String
Description: Bucket Name
EnvironmentType:
Description: 'Specify the Environment type of the stack.'
Type: String
Default: SupportSages-Test
AllowedValues:
- SupportSages-Test
- SupportSages-Prod
- SupportSages-Dev
ConstraintDescription: 'Specify either SupportSages-Test or SupportSages-Prod.'
Resources:
S3Bucket1:
Type: AWS::S3::Bucket
Properties:
AccessControl: PublicRead
BucketName: !Ref BucketNameParameter1
BucketEncryption:
ServerSideEncryptionConfiguration:
- ServerSideEncryptionByDefault:
SSEAlgorithm: AES256
VersioningConfiguration:
Status: Enabled
S3Bucket2:
Type: AWS::S3::Bucket
Properties:
AccessControl: PublicRead
BucketName: !Ref BucketNameParameter2
BucketEncryption:
ServerSideEncryptionConfiguration:
- ServerSideEncryptionByDefault:
SSEAlgorithm: AES256
VersioningConfiguration:
Status: Enabled
S3Bucket3:
Type: AWS::S3::Bucket
Properties:
AccessControl: PublicRead
BucketName: !Ref BucketNameParameter3
BucketEncryption:
ServerSideEncryptionConfiguration:
- ServerSideEncryptionByDefault:
SSEAlgorithm: AES256
VersioningConfiguration:
Status: Enabled
BucketPolicy:
Type: AWS::S3::BucketPolicy
Properties:
PolicyDocument:
Id: MyPolicy
Version: 2012-10-17
Statement:
- Sid: PublicReadForGetBucketObjects
Effect: Allow
Principal: '*'
Action: 's3:GetObject'
Resource: !Join
- ''
- - 'arn:aws:s3:::'
- !Ref S3Bucket1
- /*
Bucket: !Ref S3Bucket1
BucketPolicy:
Type: AWS::S3::BucketPolicy
Properties:
PolicyDocument:
Id: MyPolicy
Version: 2012-10-17
Statement:
- Sid: PublicReadForGetBucketObjects
Effect: Allow
Principal: '*'
Action: 's3:GetObject'
Resource: !Join
- ''
- - 'arn:aws:s3:::'
- !Ref S3Bucket2
- /*
Bucket: !Ref S3Bucket2
BucketPolicy:
Type: AWS::S3::BucketPolicy
Properties:
PolicyDocument:
Id: MyPolicy
Version: 2012-10-17
Statement:
- Sid: PublicReadForGetBucketObjects
Effect: Allow
Principal: '*'
Action: 's3:GetObject'
Resource: !Join
- ''
- - 'arn:aws:s3:::'
- !Ref S3Bucket3
- /*
Bucket: !Ref S3Bucket3
Outputs:
BucketName1:
Value: !Ref S3Bucket1
WebsiteURL1:
Value: !GetAtt [S3Bucket1, WebsiteURL]
Description: URL for website hosted on S3
BucketName2:
Value: !Ref S3Bucket2
WebsiteURL2:
Value: !GetAtt [S3Bucket2, WebsiteURL]
Description: URL for website hosted on S3
BucketName3:
Value: !Ref S3Bucket3
WebsiteURL3:
Value: !GetAtt [S3Bucket3, WebsiteURL]
Description: URL for website hosted on S3
Choose Cloudformation from AWS and click on Create stack and follow:
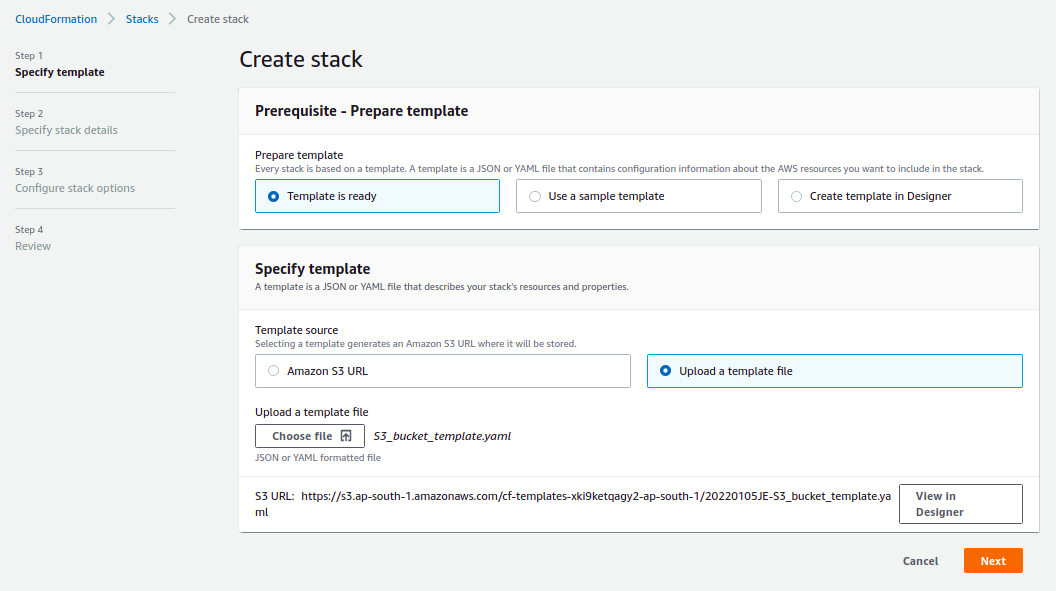
`S3_bucket_template.yaml` and click Next.
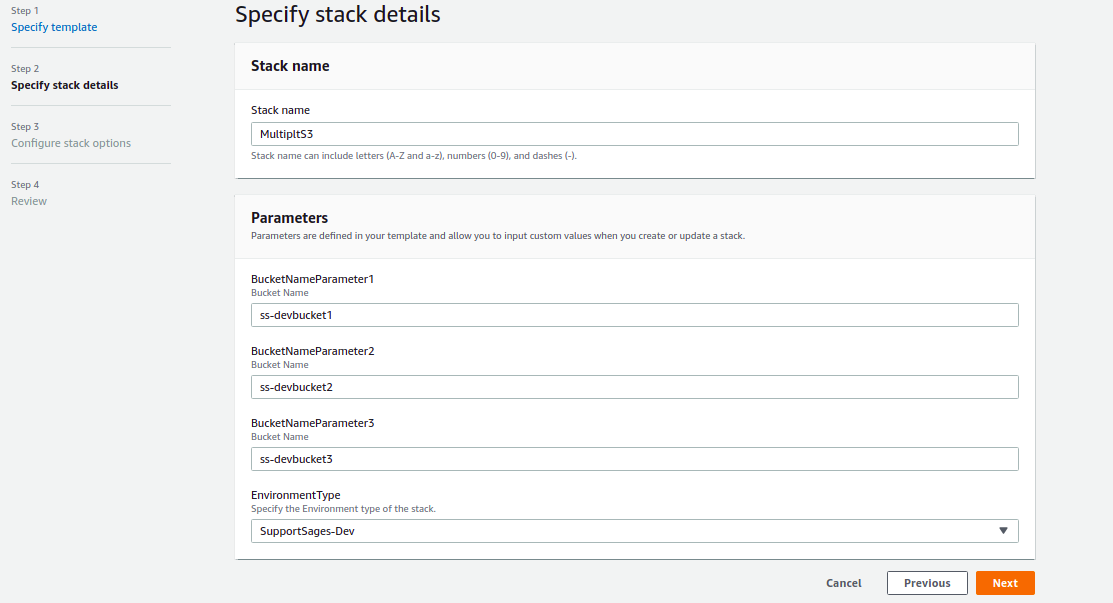
Category : AWS

Add new commentSIGN IN