Published on: December 20, 2016 by Sreenivas M

Scenario:
When one hears about phishing in websites they know that something fishy is going on with it. For all of those who doesn’t know about phishing, you may want to look into this.
Phishing is a way of getting sensitive information such as usernames, passwords, debit cards, credit card details and sometimes obtaining indirectly money by masquerading as a trusted entity.
The phishing pages may look exactly same as the original websites, when you enter your login details or other information as mentioned above thinking that it is the original site, your sensitive information are leaked and gets hacked. So, you must be very concerned about this, since you can lose your money and information.
Well, there is always someone to back you up. Google maintains a list of websites that might put innocent users like you in trouble while accessing the same. Google also analyze the sites before you enter the site to see if it’s safe and secure from phishing and other malicious activities. Sometimes your site too may got hacked and contains phishing links, google lists it as well. Such listing helps you to identify and remove the contents and identify the security vulnerabilities immediately to avoid reputation damage.
You may have seen a red web page while accessing some websites and you always know when you see a red color and what that means right, yeah! Danger. The sites that are up to no good shows the google warning page. While trying to access such sites, it may contain phishing contents, may try to install malicious software’s called malware in your computer. They may also try to trick you to install any harmful programs and causes problems when browsing online.
You are safe as long as you don’t access such sites and abstain from providing any login details there. But, if you ignore the warning page and still go in, you are looking for trouble. Your information might be leaked and your account might get hacked, so proceed at your own risk.
You may be wondering, what if google is wrong? What if it shows the red page and the website isn’t a phishing site?
Google performs regular checks and update the results regularly. This reduces the possibilities of false positives. But it doesn’t mean that it is absolute but are very low percentage of showing false positive. For malware sites, they scan sections of our web index to identify potentially compromised websites and test those sites by using a virtual machine to see if the machine gets infected. Google use statistical models to identify phishing sites.
You can find more info here
It may take around 24-72 hours for google to check the website and if its clean they will remove the warning pages. During that period, even if website owner removes all the phishing contents and make the site secure, it still may show the warning page.
If you again think your website isn’t hacked, you can always report incorrect phishing warning from the link . A sample screen shot looks like this:
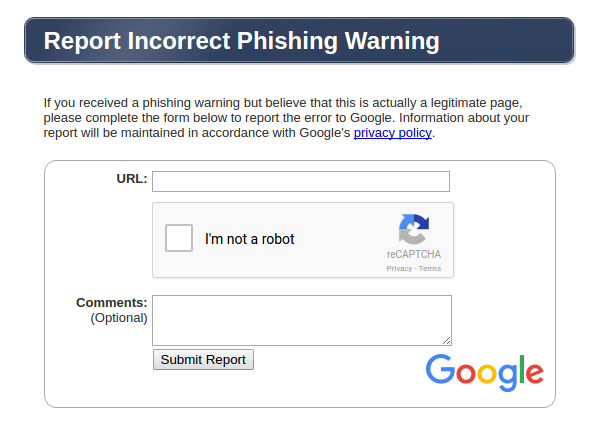
For all of those people who owns the site and was hacked, I know how it feels. Hasn’t your system administrators advised you to use strong complex passwords and change it on regular basis?
Nobody would like to go into defective page, would they? Even after you completed your part, that is updating all login credentials, doing all necessary scans and made your site secured.
Now you may be wondering, what’s next? How can I remove phishing page warning in front of my web site? Well, the answer lies in google itself. You can request them to remove the red page. You can’t just request them saying “Hey google, I have secured my site and could you please remove the red page now?”, that would be way too easy. There are some necessary steps to be followed and I am going to show you how.
Let us explore the execution of phishing content removal with a specimen case given below.
Identifying Phishing Links
If the website is having phishing contents and is listed by google, as I have said earlier, your browser would display a red page just like the one you see below. Your browser will show you “Deceptive site ahead” warning or anything similar to that. It also gives you a warning that the site is harmful and it may trick you into doing something dangerous like installing software or revealing your personal information.
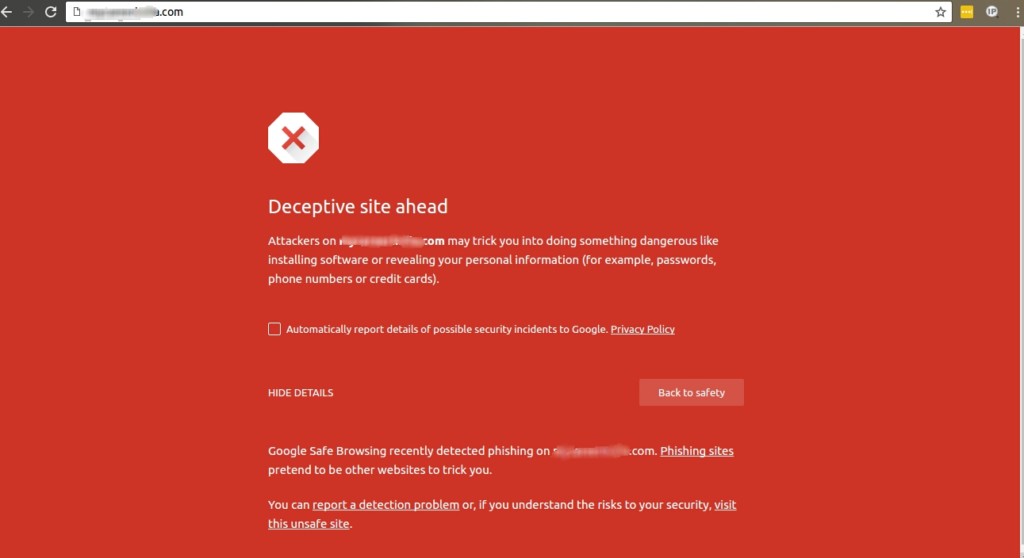
If you click on ‘visit the unsafe site’, the website would be redirected to the phishing page. In this case the phishing contents were targeted to load the google email page. As you can see from the image, the page is a replica of Gmail and you can’t be blamed for sharing your login details here in an attempt to login to your account.
How do I know if it’s a phishing page?
Well, the answer to that lies in the webpage itself. From the phishing page, if you carefully look at the URL on the top, you can see that the link is no way related to the Gmail webpage you see.
To make it simple, think it of seeing a Facebook page while typing www.google.com. That would be wired right. Yup, that’s phishing all right.
The one below shows you a phishing page.
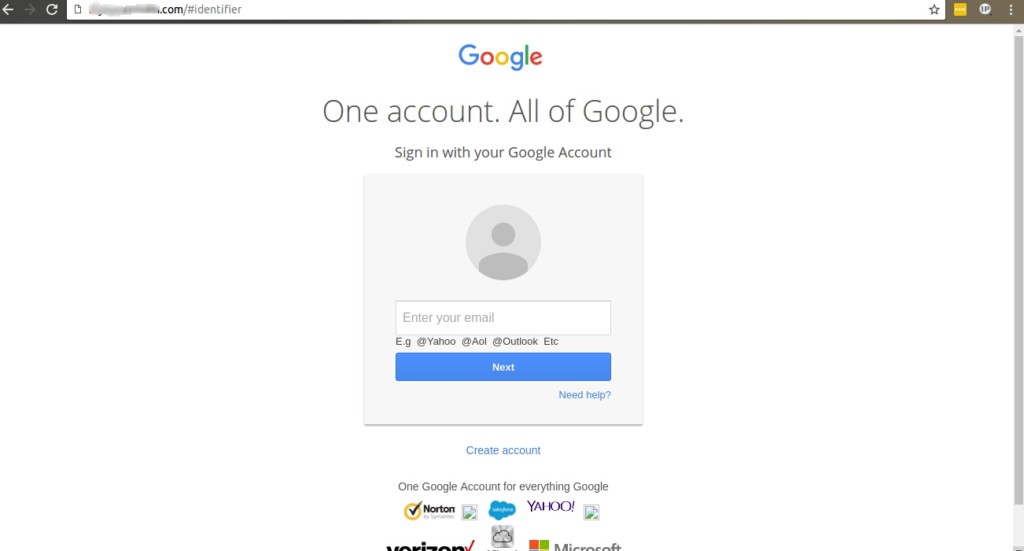
Being an end user is fine, because you are at your liberty to use the phishing site or not. But what can be done if the contents are being uploaded to your hosting account?
Definitely your prospectus as a dependable host is at sink. To avoid reputation damages, you need to clear the contents from the account. But how can you declare it to the world? The only way is to make google reverse their stand.
In such cases, we can request google to detect the harmful phishing links from the domain. To do the same, first we have to login into the Gmail account, from there you can see the google apps on the right upper menu, click on it and select the Webmaster Tools as shown.
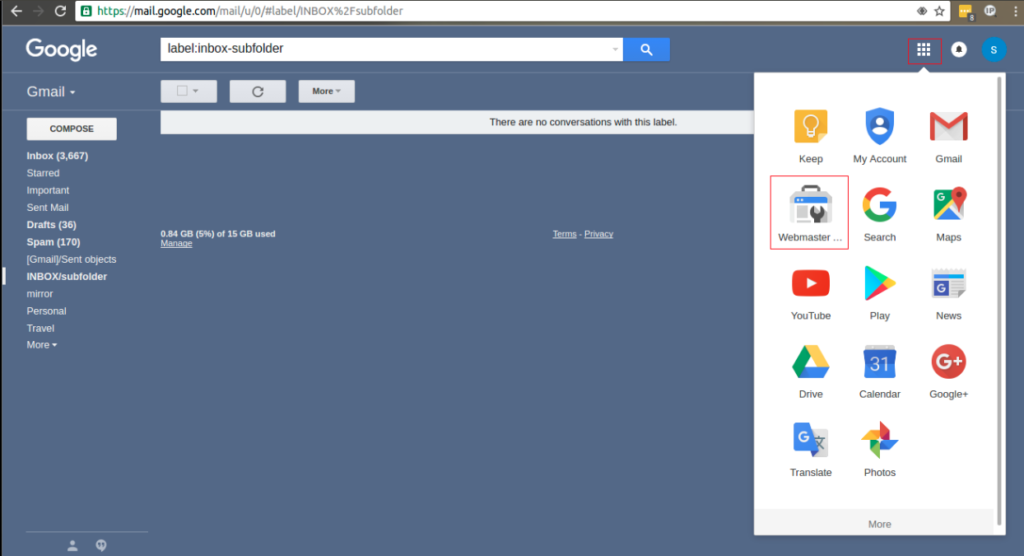
After which you will be redirected to another page, click on Add A Property box and another dialog box appears where you can enter the infected website and click add as shown below.
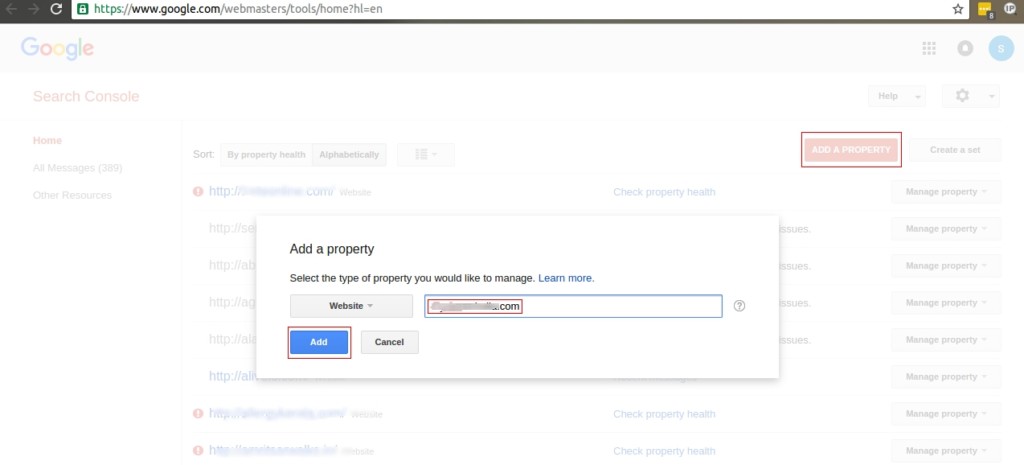
The verification process has to be done, another dialog box appears where all the instructions that have to be done is provided as shown below.
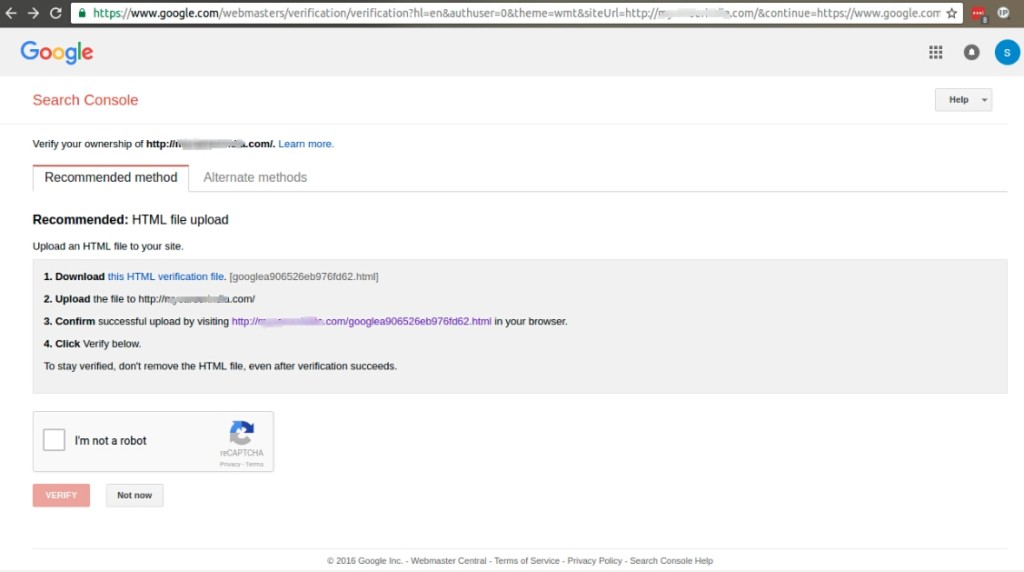
Download the verification file and the file have to be uploaded in the document root of the infected website.
For this, open the verification file and copy the contents and in the document root of the user’s directory logged in from the terminal, create a file in the name as same as the one which we recently downloaded and paste the contents and save the file as shown or the file can be uploaded via cPanel as well.
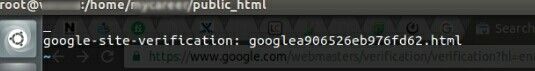
Below you can see the google verification file which has root ownership. If you try verifying the same with root access, it won’t be verified. You have to switch to the user who owns it.
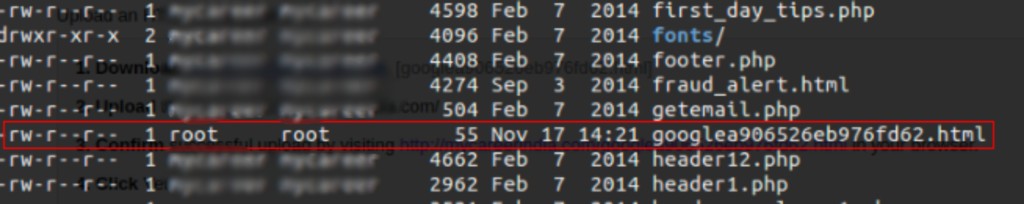
The ownership of the file which is root and changing it to user as shown:
![]()
Then you can verify by clicking the link which the google have given you in the list of steps that has to be done and you will get the following web-page.
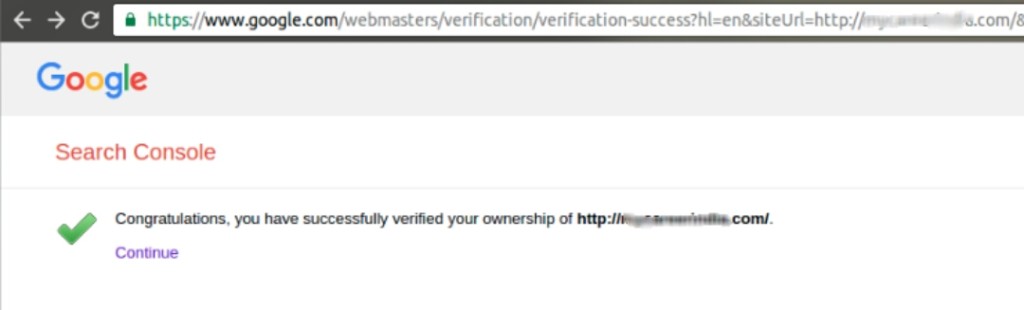
The final step is the verification, click verify once you have completed all of the given steps.
Once done, under the security Issues, you can see all the infected files as shown below:
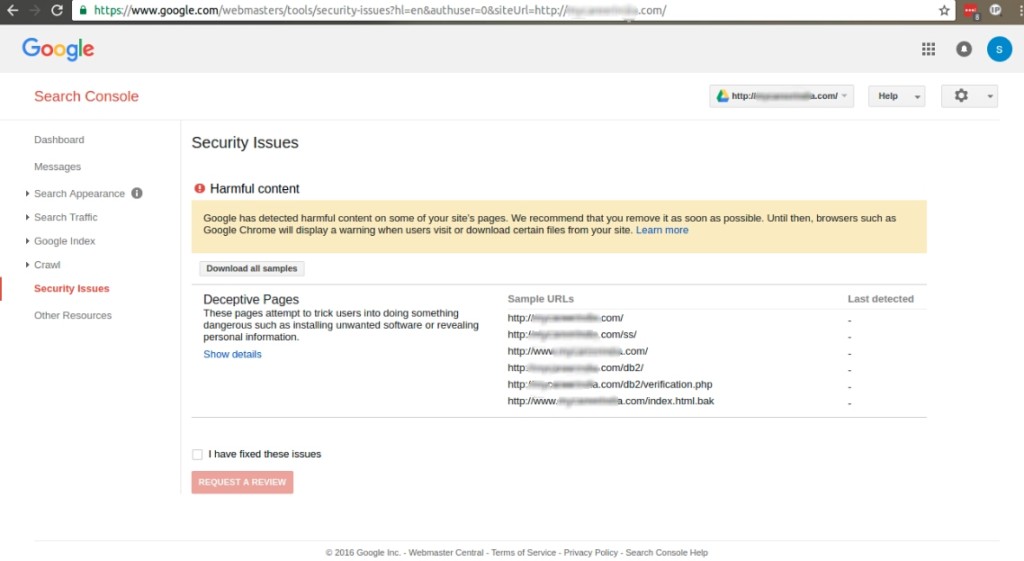
Go to the document root and change ownership of these files to 000 or remove the same if the client permits and inform the client about the files removed. Do a malware scan to see if there are anymore infected files are present.
Also, it’s better to reset the cPanel passwords, FTP passwords to make it more secured and inform the client to do regular updates.
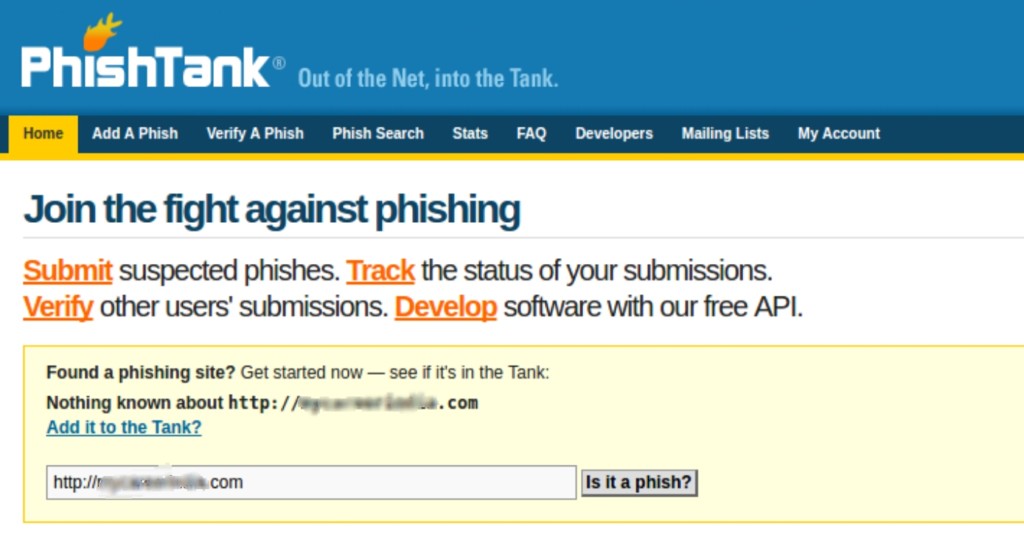
You can also go to the site www.phishtank.com and check your infected domain to see if anymore phishing sites are present as shown.
After confirming that all the infected files are removed, go to security issues and click on the Request A Review. It would take around 24-72 hours to verify by google. Once they have verified that the site is secure, they would remove the red warning page.
Category : General, Howtos, Linux, Security

Add new commentSIGN IN