Published on: April 4, 2017 by Afsal

Scenario:
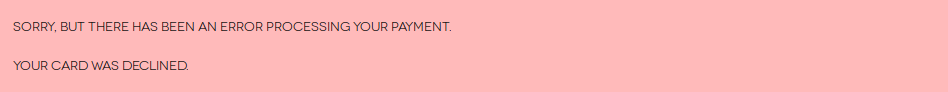
Recently, the following error was thrown whenever I try to process a payment in PayPal.
“Stripe / PayPal no longer supports API requests made with TLS 1.0. Please initiate HTTPS connections with TLS 1.2 or later”
on further investigation it is found that common payment gateways such as PayPal are updating their API servers to only accept requests made using the new TLS 1.2 protocol for encryption. This is intended to secure all external connections made to the payment gateways. Interestingly the same issue happened during Stripe checkout as well, ruling out any issues specific to PayPal alone.
Even though the server is enabled with TLS 1.2, the default connections uses TLS 1.0 for establishing connections with payment gateways and it creates the compatibility issue.
This issue was a good one. Took me 1+ hour to figure out. Google helped by lighting the path 🙂
Here is what I did.
1.Checked in the Qualys SSLLabs using the link https://www.ssllabs.com/ssltest and confirmed that TLS 1.2 is enabled.
2.Worked in the SSL settings of web server / virtual host to enable only TLS1.2 by using the following entry in my virtual host entry
SSLProtocol -all +TLSv1.2
You need to tweak it in accordance with your webserver settings. I also tried adjusting the priorities of TLS v1 TLS v 1.2 etc.
3. Checked for the latest version of OpenSSL and Curl
4. Tried matching the libcurl version in CLI and the phpinfo page and they turned out to be the same.
5. OpenSSL versions also matched in phpinfo and CLI
6. Tried running curl in the CLI with –tlsv2 option enabled. It worked there, but still not on the website.
I tried running the php script and it was returning me TLS 1.0 . So that was the turning point. For some reason system is taking TLS 1.0 and not trying to negotiate TLS 1.2
<php $c = curl_init(); curl_setopt($c, CURLOPT_URL, "https://api-tls12.stripe.com"); curl_setopt($c, CURLOPT_RETURNTRANSFER, true); $r = json_decode(curl_exec($c)); curl_close($c); echo $r->tls_version; ?>;
As anyone can guess, the issue is with the default version.
By default it is taking TLS 1.0. Issue would be solved if I can somehow get TLS v 1.2 to load. I tried setting CURLOPT_SSLVERSION, but unfortunately (or fortunately) it didn’t work 🙁
Finally an interesting discussion came as Bug 1272504 in https://bugzilla.redhat.com/show_bug.cgi?id=1272504 .
Luckily, the server was a VPS and hence we could update the package. yum update nss.i686 and the issue got resolved. The above code displayed TLS 1.2 and I knew the problem solved. It did!!
Category : Howtos, Linux, Troubleshooting

Add new commentSIGN IN